SELinux: A Mandatory Part of Running a Secure PostgreSQL Database
Data is the most critical asset of any company today. There are many recommendations to secure a PostgreSQL database, e.g. CIS Benchmark for PostgreSQL, but Linux provides already one which you should not avoid: Security-Enhanced Linux (SELinux). SELinux provides access control for files, processes and applications to grant access or deny it. This security architecture [...]
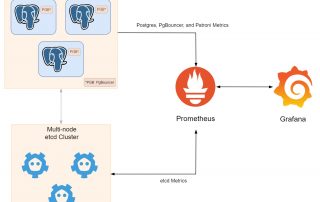
Cluster Monitoring with Prometheus & Grafana on EC2 Instances
In the previous blog post, Exporting metrics from etcd, PostgreSQL, PgBouncer and Patroni, we have prepared the endpoints for Prometheus to scrape metrics from etcd, PostgreSQL, PgBouncer and Patroni. In this blog post, we will use those endpoints to monitor the cluster with Prometheus and Grafana on EC2 instances. Prerequisites Make sure you [...]
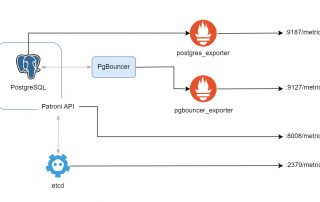
Exporting metrics from etcd, PostgreSQL, PgBouncer & Patroni
In today's complex IT landscapes, monitoring is not just a nice-to-have but a necessity. It is important to know what is going on in your systems, and to be able to react quickly to any issues that arise. In this blog post, we will look at how to expose metrics from etcd, PostgreSQL, PgBouncer [...]
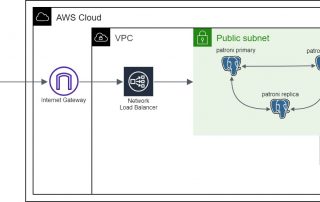
Load Balancers: Your Key to a Highly Available PostgreSQL Cluster
In our previous blog posts, we explored how to create a strong and reliable PostgreSQL cluster using Patroni and the Spilo container image. We also covered topics like connection pooling for PostgreSQL and the use of S3 buckets for backup and recovery, all of which boosted PostgreSQL's reliability and availability. Now, as we move [...]
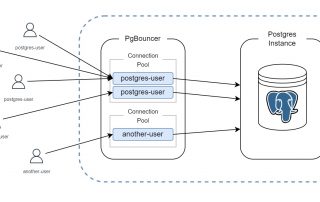
Setting up a Connection Pooler for PostgreSQL on EC2 Instances
In the world of database management, PostgreSQL stands tall as a powerful and reliable open-source relational database system. However, as database workloads grow, efficient connection management becomes crucial for maintaining performance and scalability. This is where connection poolers like Pgbouncer come into play. In this blog post, we'll explore the setup and configuration of [...]
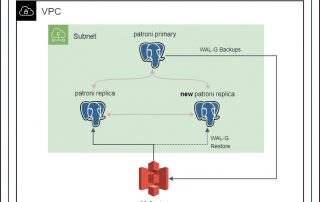
Backing up & Restoring a Highly Available PostgreSQL Cluster with S3
In our previous blog posts, Setting up a highly available PostgreSQL Cluster with Patroni using Spilo Image, we embarked on a journey to set up a highly available PostgreSQL cluster managed by Patroni using the Spilo image. We saw how Patroni, in collaboration with an etcd cluster, elevates PostgreSQL to new heights of availability [...]